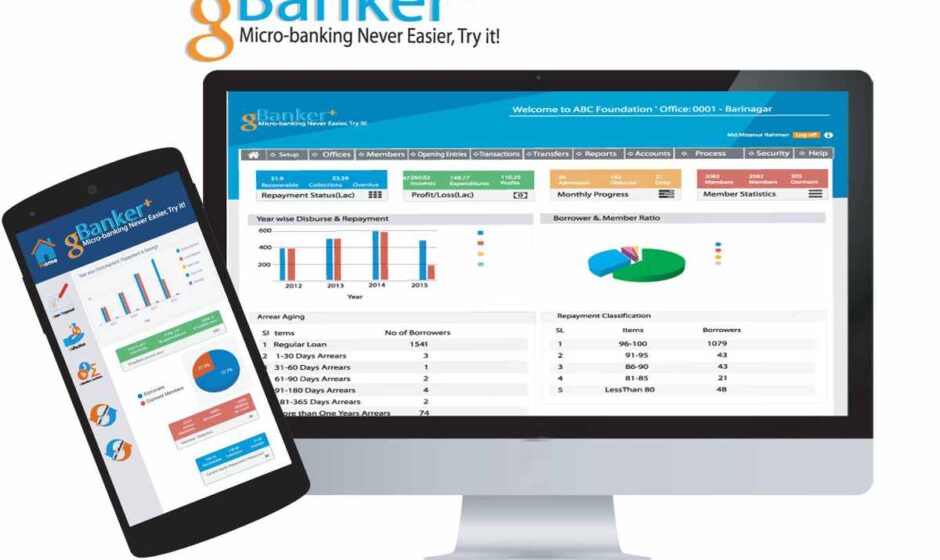
When you see an address like https://gbanker.app:8273/Account/Login?ReturnUrl=%2f you are looking at a regular web app login page using a port that’s not the usual one (8273). I won’t help you get around any site or change how it works. But I can talk about, in a straightforward way, how a banking or money management web app like this is often set up. I can help you know how logins and user profiles usually work, what kind of security is used, and what smart things people and admins should do to stay safe.
What this URL structure implies
https://— the site needs to use TLS (HTTPS) to keep traffic safe. You should always look for encrypted connections, especially when money is involved.gbanker.app— this is the domain name. It is most likely the product name or the place where it is being used.:8273— this is a high, non-standard port. People who build web apps often use ports like this for testing, inside services, or when they want to split up services on the same host. This is not a bad thing, but it can show that the site could be running in a development or special setup./Account/Login?ReturnUrl=%2f— many web frameworks use this kind of login page. The page has aReturnUrlto let users go back to the page they first wanted, once they log in.
Typical account lifecycle (user perspective)
- Registration / Invitation — A user can sign up with their email and password. They fill out a few bits about themselves. Or an admin can invite them to join. For business apps, people often need to give more details before they get all the tools. This could be their company name, tax ID, or KYC papers.
- Email check — A link is sent to the email to make sure the address is real. A person must click it. This step helps keep others from creating fake accounts. A user also needs it if they ever have to reset their password.
- Get started — A new user is asked to set up a few things like their time zone, currency, and what part they will have with the team. In business apps, users also put in the details of their group or company.
- Security setup — A user turns on 2-step checks to make their logins safer. Most use an app or text message. Admins can make the rule so all users need to have 2-step checks turned on.
- Connecting accounts — If the app works with banks, it pulls the info with a safe connector like Plaid, Yodlee, or through an API. A user might add files with their bank moves too, like CSV or OFX formats.
- Roles & who gets in — A group sets up what everyone can see or do (like admin, book
Login flow — what to expect and why it matters
- Secure transport: TLS (HTTPS) with a good certificate must be used. You should see a padlock in your browser. If there are errors about the certificate, do not go on.
- Credential submission: A username or email and password are needed. Most apps stop weak passwords and often make sure that your password was not leaked before.
- Multi-factor authentication: After your info is right, you will need another step such as a TOTP code, hardware key, or SMS. This adds more safety.
- Session management: Secure cookies—like HttpOnly, Secure, and SameSite—hold session tokens. The app should log you out after you are idle or after a set time to keep things safe.
- ReturnUrl handling: The
ReturnUrlparameter is used to send you where you want to go. But, the app should check it to stop open-redirect problems.
Security expectations (must-have practices)
If you want to trust any app with your money, it should have:
- TLS everywhere — no mixed content, good certificate, HSTS turned on.
- 2FA support — it is better to use TOTP or things like hardware keys (WebAuthn/FIDO2).
- Strong password rules and works with password managers if you want.
- Rate limiting & IP checks to stop many guessing tries.
- Session safety — short times for login, logout buttons that turn off tokens on the server.
- Audit logs that show who read or changed private data, entries that stay as they are.
- Data encryption at rest for all stored money info and personal details.
- Secure coding rules — check inputs, CSRF stop, block things like SQL injection and XSS.
- Regular security checks — scans for weak spots and checks by outside teams or bug rewards groups.
Administrative controls & operational best practices
Administrators should configure:
- Role-based access control (RBAC): split up duties for payments, reconciliation, and admin tasks.
- Least privilege: give people only the permissions they need.
- User lifecycle management: remove access for people who leave right away and set up rules for short-term access.
- 2FA enforcement: make sure MFA is turned on for all important accounts.
- Monitoring & alerting: watch for odd transfers, big downloads, or logins from places you do not expect.
- Backup & export capability: make sure you can export data (CSV, API), and test backups so you know they can be restored.
Troubleshooting common login/account issues (user tips)
- Certificate errors: do not skip them. You should talk to the person in charge or make sure you are using the right domain.
- Email not received: look in your spam, company filters, and add the sender to your safe list.
- Lost 2FA: you need to save your backup codes when you turn on 2FA. If you lose access, follow the steps from the company to get back in — you may need to prove your identity.
- Can’t connect to custom port: some company firewalls do not let you use ports that are not common; try using a different way to get online or talk to your IT team.
- Suspicious activity: right away, change your passwords, sign out of all sessions, turn on 2FA, and tell the company.
Privacy, compliance, and due diligence
Before trusting a finance app:
- Read the privacy policy to know how data is handled and shared.
- Make sure rules are followed when they apply: PCI-DSS for card use, SOC 2 for safety steps, GDPR for EU personal info, and area rules for keeping or sending money.
- Look at data export & deletion rules — you need to get your data out and ask to delete it if the law says you can.
- Get details about the company — find clear info about who they are, ways to contact them, and outside reviews.
Final checklist for users
- Check the site to see if it has HTTPS and the certificate works.
- Turn on 2FA and save your recovery codes somewhere safe.
- Make one strong password that no one else has. A password manager can help.
- See what export options are there and back up your financial data.
- Try out integrations with little bits first. Do not trust it with big transfers right away.
- Keep your software, like your browser and OS, updated. Keep an eye on your activity.
Closing
A URL such as https://gbanker.app:8273/Account/Login?ReturnUrl=%2f is common in many web apps you see these days. The ideas above — safe login steps, 2FA, handling sessions, RBAC, data protection, and strong plans for how things are run — are used in good apps where people use their money and other info. If you like, I can turn this into a full 1,000-word piece with headings and a warm feel. It will fit well for posting online (I won’t share anything secret or important that should not be public). Just tell me about the people you want to read it (is it for developers, those who run a small business, or IT admins?) and I’ll use the right words for them.